Authorization
|
Authorization feature
This page is an introduction to Authorization midPoint feature.
Please see the feature page for more details.
|
MidPoint has a very powerful and flexible authorization mechanism. This mechanism can be used to set-up complex configurations for various occasions from enterprise delegated administration to a cloud multi-tenant environment. MidPoint starting from version 3.0 has a very fine-grained authorization model. The model uses authorization statements that can be attached to roles. The authorization model can control which parts of GUI can a user access, what operations are allowed, on which objects they are allowed and for which attributes. The authorization is enforced on several levels allowing for an unprecedented flexibility while still keeping a clean and secure access control model.
The authorization model is seamlessly integrated with the RBAC mechanism. Therefore it is easy to use even a complex authorization schemas in an IDM solution. As the authorization statements are integrated with RBAC roles then they can be hierarchical (nested), they can be subject to an approval process and so on.
Authorization model of midPoint is based on the widely used subject-action-object authorization triple. However it would be quite difficult to maintain large set of authorization statements if they are maintained on just one place. Therefore we have decided to integrate midPoint authorization model with the RBAC mechanism. Authorization statements are placed inside RBAC roles. These roles are then assigned to a users. This allows very scalable and maintainable authorization set-up.
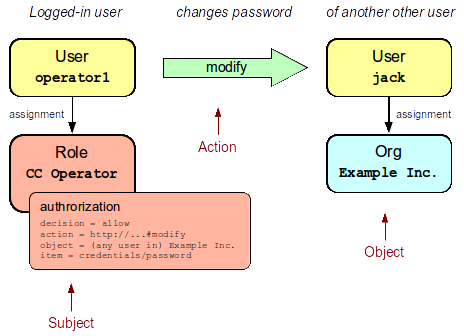
The following diagram illustrates an example of practical use of authorization statement in midPoint.
It combines authorization, RBAC and organizational structure feature to create a delegated administration set-up.
There is CC Operator role for call center operators.
This role contains an authorization statement which allows modification of password (action=modify, item=credentials/password).
This statement applies only to operations for which the object of the operation is a member Example Inc. organization.
This set-up gives the call center operators to change password of any user in Example Inc. This is a simple example of delegated administration.

Authorization concept is an integral part of midPoint architecture. Authorization are enforced at several layers of midPoint component structure to assure complete authorization coverage. This can also be utilized to create a very complex authorization schemes, e.g. enterprise delegated authorization, partial multi-tenancy, segregation of organizational units, compartmentization, etc.
The Authorization Configuration pages provides a detailed description of the configuration of midPoint authorization statements.
See Also
Compliance
This feature is related to the following compliance frameworks: