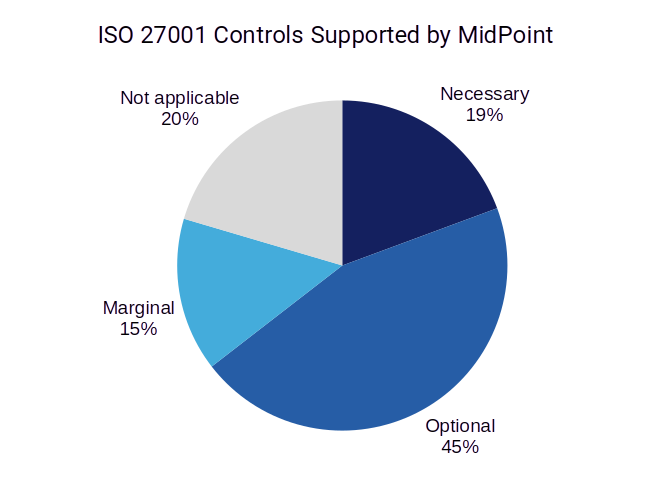
ISO/IEC 27001 Compliance
ISO/IEC 27000 Series of standards deal with information security management systems (ISMS), an essential building block of cybersecurity. The standard series describes best practice in the field, providing recommendations and guidance.
-
ISO/IEC 27000 specification provides an introduction and a vocabulary.
ISO 27000 vocabulary was mapped to midPoint vocabulary to improve understanding. Moreover, some terms of midPoint vocabulary were adapted to standard ISO27000 vocabulary.
-
ISO/IEC 27001 specification is the normative core of 27000 series. It specifies requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS). Annex A of the specification provides list of concrete information security controls.
-
ISO/IEC 27002 specification provides additional information on best practice and further guidance for implementation and maintenance of information security management system (ISMS). Controls listed in ISO 27001 Annex A are further explained in ISO 27002 document.
Statement of Applicability
Applicability (SoA) explains how midPoint can assist a company in aligning with ISO/IEC 27001:2022. While midPoint is a software tool and cannot provide compliance on its own, proper configuration can significantly aid in achieving ISO/IEC 27001:2022 compliance. This document, along with the accompanying Excel file, maps midPoint features to each ISO/IEC 27001:2022 control and evaluates the potential assistance midPoint offers for each control.
Overall, midPoint supports 74 out of 93 (~80%) controls specified by ISO 27001, although the level of midPoint support varies.
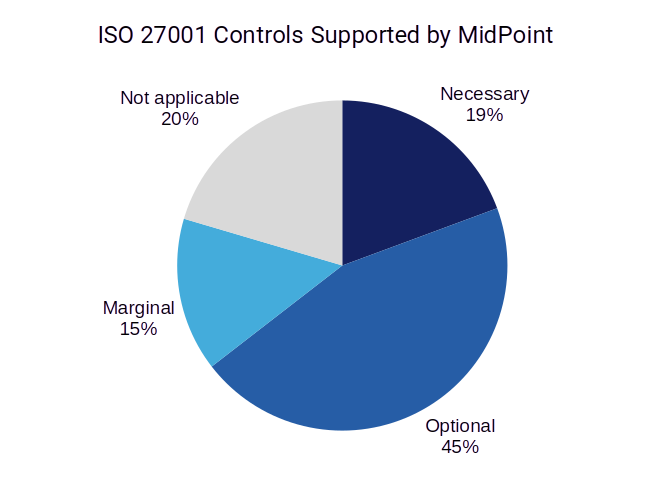
Mapping of MidPoint Features
| This list applies to the latest stable release of midPoint starting with midPoint 4.9.1. |
| Control ID | Control Name | Necessity | Implementation Overview | Number of Features |
|---|---|---|---|---|
| 5.1 | Policies for information security | optional | MidPoint can provide data for building security policies. | 7 |
| 5.2 | Information security roles and responsibilities | necessary | MidPoint provides essential management capabilities of roles and responsibilities by using its advanced role-based access control (RBAC) mechanisms. | 15 |
| 5.3 | Segregation of duties | necessary | MidPoint can manage, monitor and enforce segregation of duties (SoD) policies through the organization. | 7 |
| 5.4 | Management responsibilities | not-applicable | - | |
| 5.5 | Contact with authorities | not-applicable | - | |
| 5.6 | Contact with special interest groups | not-applicable | - | |
| 5.7 | Threat intelligence | not-applicable | - | |
| 5.8 | Information security in project management | necessary | MidPoint can manage projects as organizational units, including project governance information (managers, sponsors, reviewers). | 11 |
| 5.9 | Inventory of information and other associated assets | optional | MidPoint can manage applications, roles and entitlements that are closely related to assets. | 12 |
| 5.10 | Acceptable use of information and other associated assets | necessary | Access control mechanisms of midPoint can be used to manage and record access rights information. | 12 |
| 5.11 | Return of assets | marginal | MidPoint can record ownership of devices, tokens and licenses using the concept of "service". | 7 |
| 5.12 | Classification of information | necessary | MidPoint has a native information classification feature, which can be used to set up classification and clearance schemes. | 11 |
| 5.13 | Labelling of information | optional | Applications can be classified using the defined classification scheme. | 5 |
| 5.14 | Information transfer | optional | MidPoint can use classifications and policy rules to limit and partially control information transfer. | 8 |
| 5.15 | Access control | necessary | The policy-driven role-based access control mechanism of midPoint can be used as a solid framework for a topic-specific policy on access control, especially the Policy-driven RBAC mechanism. | 26 |
| 5.16 | Identity management | necessary | MidPoint platform with all of its features is designed to support identity management and all its aspects. | 50 |
| 5.17 | Authentication information | necessary | MidPoint is designed to manage authentication information, especially passwords. | 8 |
| 5.18 | Access rights | necessary | MidPoint is an essential component to make sure access to information is provisioned, reviewed, modified and removed in accordance with policies. | 28 |
| 5.19 | Information security in supplier relationships | optional | Supplier identities can be managed by midPoint, including their access rights and relation to supplier organizations. | 19 |
| 5.20 | Addressing information security within supplier agreements | optional | Some of the supplier contractual agreements can be enforced by midPoint policies. | 11 |
| 5.21 | Managing information security in the ICT supply chain | marginal | MidPoint can provide inventory of applications, including their classifications. | 6 |
| 5.22 | Monitoring, review and change management of supplier services | marginal | MidPoint can provide some monitoring and inventory capabilities for applications. | 6 |
| 5.23 | Information security for use of cloud services | optional | MidPoint can automatically manage access to cloud services. | 16 |
| 5.24 | Information security incident management planning and preparation | optional | MidPoint can provide useful information for preparation of incident management plans. MidPoint roles can be used to pre-configure emergency access control which can be used during incident response. | 14 |
| 5.25 | Assessment and decision on information security events | marginal | MidPoint can provide supplementary information for security event classification. | 5 |
| 5.26 | Response to information security incidents | necessary | MidPoint provides essential information for incident response, as well as rapid immediate actions to contain the incident and ensure business continuity. | 18 |
| 5.27 | Learning from information security incidents | optional | MidPoint can provide essential information for ex-post investigation and processing of incidents, covering both the actions of attackers and responders. | 8 |
| 5.28 | Collection of evidence | marginal | MidPoint is one of important sources of evidence for incident investigation. Additionally, midPoint access control capabilities can be used to preserve evidence. | 7 |
| 5.29 | Information security during disruption | optional | MidPoint maintains all policies and rules during incident response. Pre-configure emergency access control can be used during incident response. Synchronization can be used to restore security after disruption. | 16 |
| 5.30 | ICT readiness for business continuity | optional | MidPoint can be used to quickly prepare replacement systems in case of disruption. Pre-configure emergency access control can be used during incident response. | 23 |
| 5.31 | Legal, statutory, regulatory and contractual requirements | optional | MidPoint documentation provides overview and guidance for compliance with several compliance frameworks. Integral documentation of midPoint can be used to document fulfillment of specific compliance requirements. | 12 |
| 5.32 | Intellectual property rights | optional | MidPoint can provide data essential for management of licenses and other intellectual property rights. | 7 |
| 5.33 | Protection of records | optional | MidPoint has several mechanisms to ensure long-term retention of essential information. | 12 |
| 5.34 | Privacy and protection of PII | necessary | MidPoint provides features that are necessary for maintaining privacy at scale, especially when dealing with consumer identities, external collaborators and similar broad user communities. | 22 |
| 5.35 | Independent review of information security | not-applicable | - | |
| 5.36 | Compliance with policies, rules and standards for information security | necessary | MidPoint provides many essential capabilities for verifying, reviewing and demonstrating compliance, as well as implementation of corrective actions. | 10 |
| 5.37 | Documented operating procedures | optional | MidPoint has built-in documentation capabilities that assist in documenting operation procedures and responsibilities. | 8 |
| 6.1 | Screening | optional | Capabilities to manage identity lifecycle, clearances and enforce policy rules are instrumental in enforcing effects of personnel screening by midPoint. | 10 |
| 6.2 | Terms and conditions of employment | not-applicable | - | |
| 6.3 | Information security awareness, education and training | optional | MidPoint capabilities provide convenient support for security trainings, re-trainings, enforcing access policies and spreading of cybersecurity awareness. | 9 |
| 6.4 | Disciplinary process | optional | MidPoint can be used as a tool to easily reduce access rights of users that violate the policy. | 8 |
| 6.5 | Responsibilities after termination or change of employment | necessary | Identity lifecycle and policy-driven role-based access control (PD-RBAC) mechanism are instrumental in handling privileges in termination/change situations. | 15 |
| 6.6 | Confidentiality or non-disclosure agreements | optional | Information classification and clearance mechanism can be used to enforce the presence of appropriate agreements. | 12 |
| 6.7 | Remote working | optional | MidPoint has mechanisms to set up access for remote work, and automatically de-provision it when not needed. | 9 |
| 6.8 | Information security event reporting | optional | MidPoint provides features that can provide security event details if necessary. | 7 |
| 7.1 | Physical security perimeters | marginal | MidPoint can provide a supportive role, recording physical perimeters for applications. | 4 |
| 7.2 | Physical entry | optional | MidPoint can provide a degree of automation regarding management of physical access tokens, especially with respect to their revocation. | 17 |
| 7.3 | Securing offices, rooms and facilities | marginal | MidPoint can control access privileges for directories. | 4 |
| 7.4 | Physical security monitoring | optional | MidPoint can control access to surveillance and alarm systems. | 5 |
| 7.5 | Protecting against physical and environmental threats | not-applicable | - | |
| 7.6 | Working in secure areas | not-applicable | - | |
| 7.7 | Clear desk and clear screen | not-applicable | - | |
| 7.8 | Equipment siting and protection | not-applicable | - | |
| 7.9 | Security of assets off-premises | optional | MidPoint provides mechanisms to manage non-human identities, such as mobile devices. | 9 |
| 7.10 | Storage media | not-applicable | - | |
| 7.11 | Supporting utilities | not-applicable | - | |
| 7.12 | Cabling security | not-applicable | - | |
| 7.13 | Equipment maintenance | not-applicable | - | |
| 7.14 | Secure disposal or re-use of equipment | optional | MidPoint provides mechanisms to manage non-human identities, which can be used to track equipment and its reuse. | 9 |
| 8.1 | User endpoint devices | optional | MidPoint provides mechanisms to manage non-human identities, which can assist in management of user endpoint devices. | 13 |
| 8.2 | Privileged access rights | necessary | MidPoint has numerous features to support management of privileged access rights. | 31 |
| 8.3 | Information access restriction | necessary | MidPoint is an essential tool for managing information access restriction, supporting it with numerous features. | 27 |
| 8.4 | Access to source code | necessary | MidPoint can manage access control settings of source code management systems, CI/CD and testing platforms and other software development systems. | 20 |
| 8.5 | Secure authentication | optional | Although midPoint does not deal with most authentication aspects directly, it is an important system to support authentication policies indirectly. | 11 |
| 8.6 | Capacity management | marginal | MidPoint provides supporting information and tools for capacity management. | 8 |
| 8.7 | Protection against malware | marginal | MidPoint has a couple of supporting functionalities for malware protection. | 6 |
| 8.8 | Management of technical vulnerabilities | marginal | MidPoint has some functionalities to support policies related to vulnerability management. | 5 |
| 8.9 | Configuration management | necessary | MidPoint is an essential component for security configuration management. | 22 |
| 8.10 | Information deletion | optional | MidPoint provides automation of personal data deletion through identity lifecycle management. | 5 |
| 8.11 | Data masking | optional | Provisioning flexibility of midPoint can be used to provide some data masking capabilities. | 9 |
| 8.12 | Data leakage prevention | marginal | MidPoint can provide supporting information for data leakage prevention. | 6 |
| 8.13 | Information backup | optional | MidPoint contains up-to-date access control information which is essential for reliable restore procedures. | 9 |
| 8.14 | Redundancy of information processing facilities | optional | MidPoint provides synchronization functions for access control information in redundant components. | 9 |
| 8.15 | Logging | optional | MidPoint records all activity in the audit trail. | 5 |
| 8.16 | Monitoring activities | optional | MidPoint provides numerous features for monitoring of identity-related configuration, and few features to support other monitoring systems. | 11 |
| 8.17 | Clock synchronization | not-applicable | - | |
| 8.18 | Use of privileged utility programs | optional | MidPoint provides capabilities for management of rules and policies for accessing privileged utility programs. | 12 |
| 8.19 | Installation of software on operational systems | optional | MidPoint provides supporting mechanisms for management of software on operational systems. | 14 |
| 8.20 | Networks security | optional | MidPoint provides important capabilities for management of access to network devices. | 10 |
| 8.21 | Security of network services | optional | MidPoint can manage access to administration privileges of network services. | 9 |
| 8.22 | Segregation of networks | not-applicable | - | |
| 8.23 | Web filtering | marginal | MidPoint provides minor supporting functionality for web filtering. | 2 |
| 8.24 | Use of cryptography | not-applicable | - | |
| 8.25 | Secure development life cycle | optional | MidPoint provides access control and policies supporting secure software development. | 6 |
| 8.26 | Application security requirements | optional | MidPoint provides numerous features for addressing common application security requirements. | 9 |
| 8.27 | Secure system architecture and engineering principles | necessary | Identity governance and administration (IGA) platform such as midPoint is an essential component of secure system architecture. | 2 |
| 8.28 | Secure coding | marginal | MidPoint can manage access to development environments and tools. | 6 |
| 8.29 | Security testing in development and acceptance | not-applicable | - | |
| 8.30 | Outsourced development | not-applicable | - | |
| 8.31 | Separation of development, test and production environments | optional | MidPoint has mechanisms to control access to individual environments, as well as access exclusion mechanisms. | 11 |
| 8.32 | Change management | optional | MidPoint has numerous features that take part in management of identity-related changes. | 19 |
| 8.33 | Test information | marginal | MidPoint provides supporting functionality for test information protection. | 3 |
| 8.34 | Protection of information systems during audit testing | optional | MidPoint can use access control mechanisms to manage auditor access to systems. | 10 |