Advanced search - EXAMPLES
|
Since 4.4
This functionality is available since version 4.4.
The functionality was further improved in versions 4.5, 4.6, 4.7, 4.8.
|
Midpoint provides multiple mechanisms to query the data and search for information. This document provides basic information and examples of advanced search using midPoint query language in midPoint GUI.
The document is intended for users who understand midPoint concepts and architecture (IDM operators, administrators, engineers,…). They can use the midPoint query language in deeper analysis and searching for the objects and their relations in GUI.
| The new query language is undergoing rename from 'Axiom' to 'midPoint Query Language' since midPoint version 4.8. As the Axiom name is well known, it can be still for some time referenced also with this name. Please consider Axiom Query Language and midPoint Query Language as synonyms. |
Basic Information
MidPoint Query Language is designed to query objects in midPoint repository. It is a universal language used to search for objects in the repository, filter objects, set up object references and so on. The language closely follows midPoint data model. Names of the properties, attributes and all the data items are directly taken from midPoint data model (e.g. fullName, activation/effectiveStatus).
MidPoint Query Language provides following comparison operators: "=", "!=", "<", "⇐", ">", ">=" with their usual meaning. Strings may be compared also with "startsWith", "endsWith", "contains" and "fullText" operators (note: fullText operator requires configuration of fulltext index).
It provides also logical operators "and", "or" and "not". Execution of complex queries may be ordered using brackets "(" and ")".
Objects in midPoint are bound by relations (assignments, inducements, ..). MidPoint Query Language provides dereferencing mechanism with operator "@" which allows searching objects using attributes and values in the references. See examples below for usage.
You can create complex queries also using "matches" operator and "exists" operator. See examples below for their usage.
More detail information and description of the operators can be found at midPoint Query Language documentation.
How to start
Basic search query is shown above each view by default. User can switch to advanced query by clicking the query button and selecting the Advanced option.
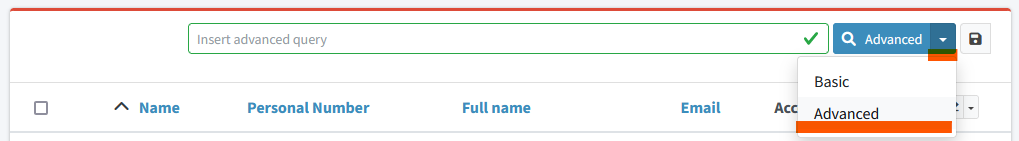
Each query is searching objects within currently opened view in GUI. If user needs to search all objects of specific type, he has to select the relevant view (All users, All roles, All services).
Knowledge of internal structure of midPoint objects is necessary - at least basic names of attributes and basic understanding of assignment/targetRef attribute and roleMembershipRef attribute. If the user needs to find name of specific attribute, he can use Edit raw button on the object details page.
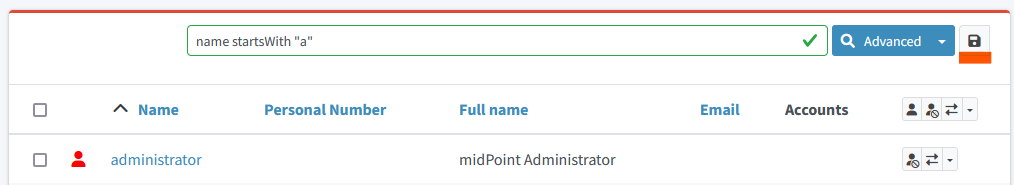
Search queries are case-sensitive. Query givenName = "John" is different from givenName = "john"
Saved searches
User can save predefined useful filters for future use - by using Save filter button.
Advanced Query Examples
Examples of queries using midPoint Query Language.
Search by attributes in objects and references
| Request | Advanced query | Details |
|---|---|---|
Find users with specific given name |
|
|
Find users with last name starting with specific string |
|
|
Find roles with name ending with specific string |
|
Searching in All roles view |
Find service where Application URL extension attribute contains specific string. |
|
Attributes specific for the deployment are in objects stored as extension attributes in <extension> XML element. To search these attributes you need to include "extension/" in the attribute name. |
Find disabled users in All users view |
|
|
Search by attributes in referenced objects |
||
Find User with specific assignment |
|
The dereferencing operator "@" states that everything behind relates to the referenced object. |
Find User with service object indirectly assigned |
|
The indirect assignment of service object represents "access to application" |
Find users of specific archetype |
|
|
Logical operators in search |
||
Find all external users with specific given name. |
|
|
Search by dates and times |
||
Find all users created after particular date |
|
|
Find all users created on particular date (e.g. 19/10/2022) |
|
createTimestamp is datetime value. The value with time is larger just the date. 2022-10-22T01:05:13 that is larger than "2022-10-22" |
Find users modified in specific second |
|
|
Search through assignments or inducements
These searches are valid in views listing objects - users, roles, services. For searches in the object panels see below.
| Request | Advanced query | Details |
|---|---|---|
Find users with specific roles directly assigned |
|
|
Find users with specific role assigned (directly or indirectly) |
|
roleMembershipRef contains both direct and indirect assignments. Note: roleMembershipRef may not be up-to-date if the role definition was updated and it’s members were not recomputed. |
Find users without any service assigned (directly or indirectly) |
|
roleMembershipRef contains both direct and indirect assignments. |
Find users without any role or service assigned (directly or indirectly) |
|
|
Roles without any inducement |
|
exists operator with not operator together. |
Find users without any role or service directly assigned |
|
Assignment attribute contains direct assignments only. Query is rather complex, because each user has at least one assignment assigned - archetype assignment. |
Users with account on specific resource |
|
Resource is identified by OID Note: For detail explanation of the query please check additional introduction to midPoint Query Language page. |
Users with account on specific resource |
|
Like previous query, just the resource is identified by resource name. |
Users having with role with specific extension attribute assigned |
|
This is a complex query: Searching for all assignments of a role identified by value of specific extension attribute. |
Referencing (supported since version 4.6) |
||
In roles view, find all roles that are assigned to specific user |
|
Dot is important in the query. |
Searching in All accesses panel
View in "All accesses" panel displays content of "roleMembershipRef" attribute. So name of this attribute must be excluded from the queries.
|
Since 4.7
This functionality is available since version 4.7.
|
| Request | Advanced query | Details |
|---|---|---|
All assigned roles |
|
You can also use ServiceType for services or OrgType for organizational units. |
All accesses starting with gallery in the display name |
|
The view shows display names of the objects. So search for name element could bring confusing results if name and displayName are different. |
All applications where the user has access |
|
This searches for all references with archetype named "Application". The same way you can search for "Application role" or "Business role". |
Searching in Assignments panels
Views in assignments panels display content of the "assignment" attribute. So name of this attribute must be excluded from the queries.
|
Since 4.7
This functionality is available since version 4.7.
|
| Request | Advanced query | Details |
|---|---|---|
All roles assigned directly |
|
|
All assignments (roles or other) with name starting with "C" |
|
Dereferencing (search with @) is working in the assignment panel only when repository search is enabled. |
Searching in Tasks
Standard structure of the task object was not prepared for searching.
Therefore, additional element affectedObjects allowing convenient searching of the tasks by affected objects and their execution mode was induced in 4.8.
|
Since 4.8
This functionality is available since version 4.8.
|
| Request | Advanced query | Details |
|---|---|---|
All tasks acting on users |
|
|
All tasks performing reconciliation |
|
Include namespace specification "c:" in the activity type. |
All tasks performing any operation with the resource XYZ |
|
|
All tasks performing reconciliation on the resource XYZ |
|
You can use archetype and resource OIDs as well, just using dereferenced names is easier to read. |
All simulation tasks |
|
Simulation tasks are in the "preview" mode. Standard tasks that also execute changes have execution mode "full". |
Searching in Audit Events
You can utilize midPoint Query Language as well in Audit Log Viewer. It will allow you to review for failed events, select specific objects and operations.
Instead of basic search, there is no specific timeframe defined for each search. Please use timestamp specification while searching in audit. It will increase search speed significantly. Especially in large audit searches.
The search in deltas is available since version 4.8.
|
Since 4.8
This functionality is available since version 4.8.
|
| Request | Advanced query | Details |
|---|---|---|
All events initiated by specific user |
|
|
All events related to specific user |
|
This is also possible via object OID, without dereferencing: |
All events in specific day |
|
|
All events within specific time range |
|
|
All events of specific type |
|
|
All events where specific attribute was updated. |
|
Include "c:" prefix to the name of the attribute. |
All failed events since specific date |
|
You can’t use scripting in GUI search. Therefore, the dates must be defined explicitly and updated if necessary. |
All events related to resource "XYZ" |
|
This is also possible via resource OID, without dereferencing: |
All events related to account "john" on the resource "XYZ" |
|
Delta components - "resourceName" and "objectName" contain values relevant during the event creation. These may be modified afterwards. |
All events related to user "JohnDoe" on the resource "XYZ" |
|
The previous select was searching of the modification of the defined account on the defined resource. This search is providing audit events on the specified resource related to specific user (not only accounts, but may be also entitlements or accounts with different names) |
All events generated by specific task (any run) |
|
|
All events generated by specific task (single run) |
|
The task identifier is individual for each run of the task. |
All object modifications that didn’t went well |
|
|
All events where accounts on the resource "XYZ" were created or modified |
|
See Also
-
midPoint Query Language - Main page of midPoint Query Language.
-
Searchable items - Which items/elements/attributes can be searched.
-
Errors while using midPoint query - Error messages with explanation and hints how to solve them.
-
Using expressions in midPoint Query language - Expressions in midPoint Query Language.